Virtual Industrial Cybersecurity Lab – Part 0: Road to Virtualization
One of the greatest entry barriers to the Industrial Cybersecurity word is the high cost associated with the acquisition of equipment (and software licenses) needed in order to have a real experience interacting with technologies and processes of the OT environment. The use of virtualization is a great way to overcome that hurdle, and start getting familiar with the protocols and particularities of the ICS world with a very low initial investment.
With this idea in mind, the objective of this laboratory is to create a fully virtual environment that makes use of several elements traditionally used in OT in order to simulate a simple automation process, that will be used later on as a testbed.
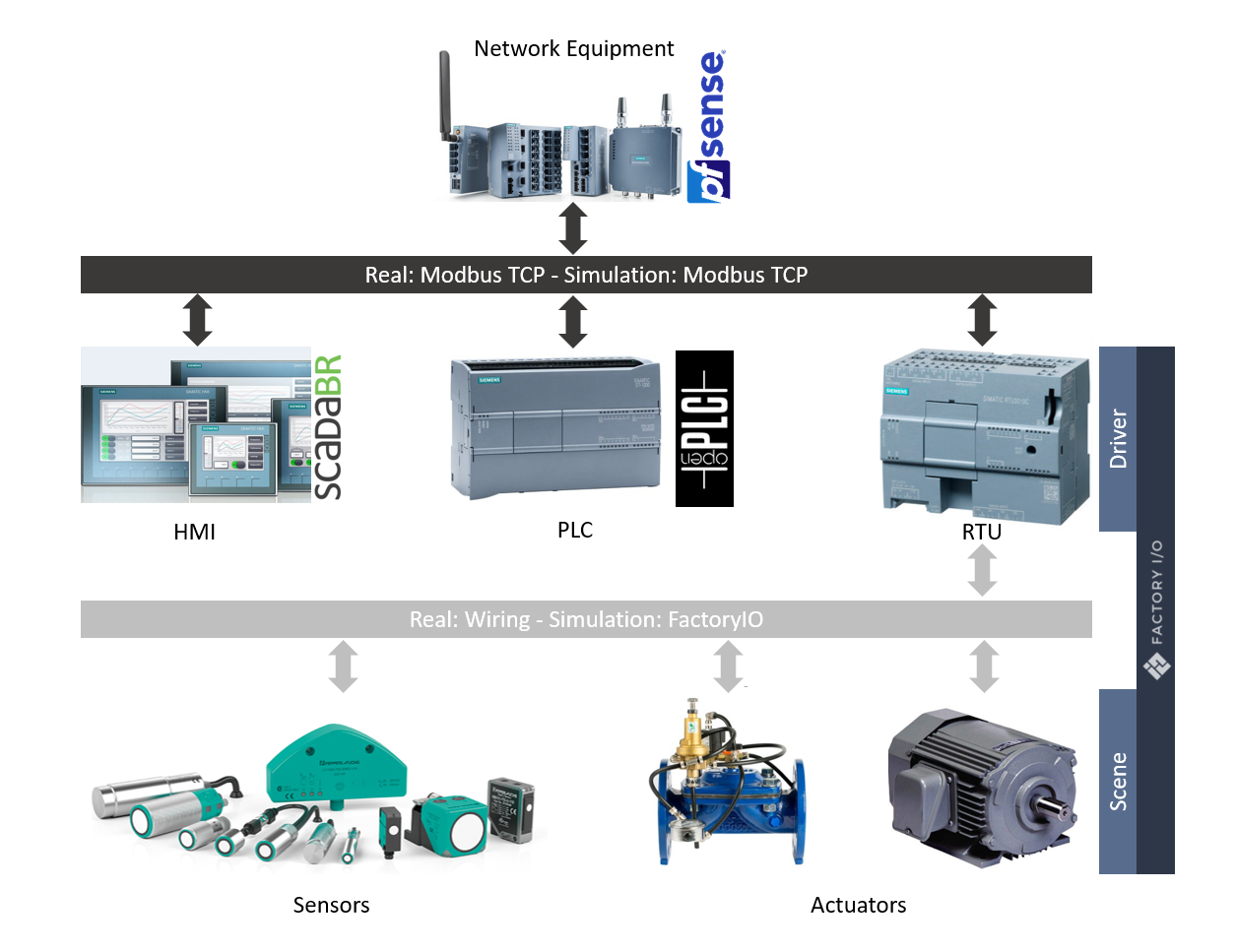
The following components will be used to implement this design:
- Three (3) virtual machines to simulate the router, the PLC, and the HMI
- Factory IO to simulate the RTU and the physical process
- The attacker is assumed to have already access to the network, so it will be represented by an additional virtual machine
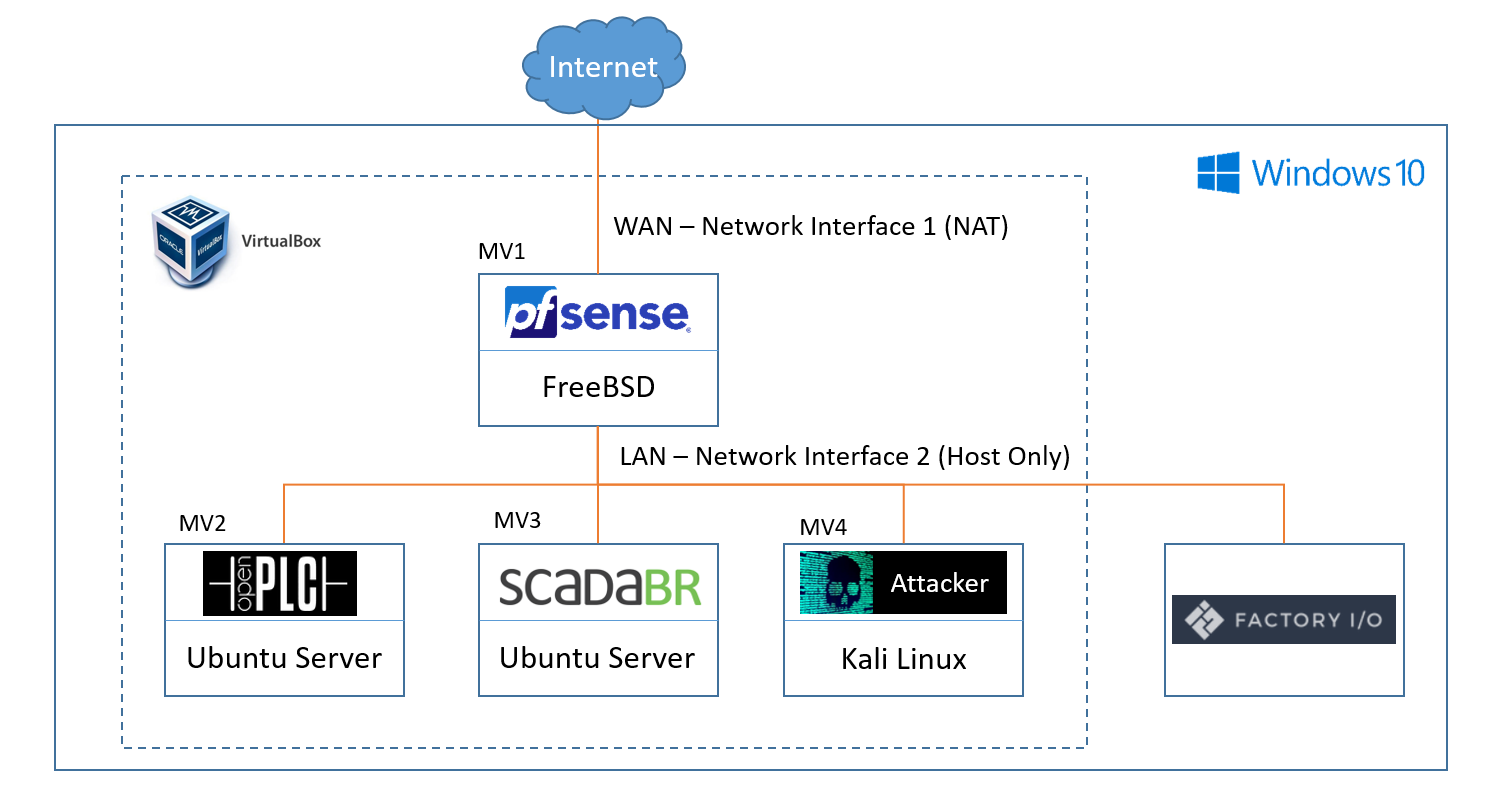
The project will have 2 differentiated workstreams: the first one will cover the deployment and configuration of all the systems required for the simulation, the second will use those systems as a testbed for different attacks and techniques. This leaves us with the following plan:
Deployment and configuration of the Virtual Industrial Cybersecurity Lab
- Installation and configuration of virtual router pfSense
- Installation of OpenPLC and ScadaBR
- Simulation of the physical process in FactoryIO
- Program the control logic, and integration of OpenPLC with FactoryIO
- Installation of the attacker machine
- Program a simple HMI that interacts with OpenPLC
Attacking the Industrial Control Systems
- Reconnaissance: Dissecting OpenPLC’s Modbus TCP communications
- Exploitation: Modbus TCP packet injection with Scapy
Each one of these points will be treated individually in a different blog entry that will be released during the development of the project.