IoT Network Segmentation Guide – Part 1: Design
The next logical step in the Homelab journey is to learn about networking and network security. Coincidentally, this is one of the topics that translates really well to the world of OT security and therefore it makes sense to dedicate its own post.
If we look at Robert M.Lee’s “Sliding Scale of Cybersecurity” one can see that architecture is generally portrayed as one of the most cost-effective passive security measures.
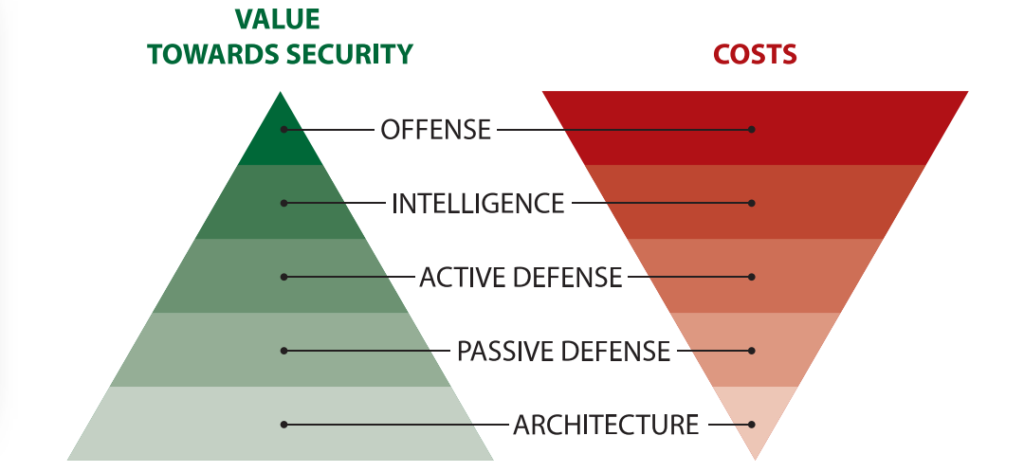
While I agree with that statement in general, I think it is only applicable for new setups, as the cost of analyzing communication flows in an existing environment, changing the network infrastructure, and applying a proper segmentation is something quite expensive in terms of resource consumption for planning, factory downtime, and general implementation costs. Therefore I greatly recommend not to fall into the temptation of postponing this step (however tempting it may be), and design a proper layout in the early stages of a project (Industrial or otherwise).
With this in mind, I used the Purdue architecture as a starting point for the segmentation design but took a lot of “artistic licenses” for the sake of operation simplification, and in order to accommodate certain hardware limitations (which is a very realistic situation in real projects). You will see later that the final setup looks nothing like Purdue. However but having high standards as a reference usually results in a better product than otherwise. The game plan is as follows:
- Identify assets
- Identify physical connectivity capabilities
- Wireless type
- 5GHz: more speed for the endpoints
- 2.4GHz: more penetration and coverage
- Ethernet type
- Wireless type
- Identify communication flows
- To internal resources
- To the Internet
- Identify additional requirements, in my case:
- Use my own local DNS server with filtering capabilities (privacy and security)
- Route traffic from as many networks as possible through a VPN (privacy)
- Group assets into functionally similar families, for me:
- Internal resources: NAS, hypervisor, networking equipment
- Trusted wireless devices that require access to internal resources: PCs, phone, tablets, etc.
- Devices that require clean Internet connectivity and do not need to access internal resources: work laptop, work phone, Fire TV Stick, etc.
- IoT devices that require Internet connectivity
- IoT devices that do not require Internet connectivity
After all those considerations, we would end with something like this:
| VLAN | Description | Connectivity | Characteristics | DNS Filtering | VPN Routing |
|---|---|---|---|---|---|
| 192.168.10.0/24 | Internal resources | Wired Wi-fi: SSID 1 | 1Gb | Yes | No |
| 192.168.20.0/24 | Trusted devices | Wired Wi-fi: SSID 2 | 5GHz (preferred) 2.4GHz | Yes | Yes |
| 192.168.30.0/24 | Clean Internet access | Wi-fi: SSID 3 | 5GHz (preferred) 2.4GHz | No | No |
| 192.168.40.0/24 | Local IoT | Wi-fi: SSID 4 | 2.4GHz | Yes | Not Applicable |
| 192.168.50.0/24 | Cloud IoT | Wi-fi: SSID 5 | 2.4GHz | Yes | Yes |
However, at this point, the real world kicks in because:
- I do not want to have 5 different SSIDs and passwords at home and, even if I wanted, my router/AP (Unifi Dream Machine) only supports a maximum of 4 SSIDs
- I will limit internal resources to wired connectivity for performance
- All IoT devices will be assigned to the same subnet, but devices that do not need Internet connectivity will have that capacity disabled via firewall rules later on
With all those considerations, this is the final setup:
| VLAN | Description | Connectivity | Characteristics | DNS Filtering | VPN Routing |
|---|---|---|---|---|---|
| 192.168.10.0/24 | Internal resources | Wired | 1Gb | Yes | No |
| 192.168.20.0/24 | Trusted devices | Wired Wi-fi: SSID 1 | 5GHz (preferred) 2.4GHz | Yes | Yes |
| 192.168.30.0/24 | Clean Internet access | Wi-fi: SSID 2 | 5GHz (preferred) 2.4GHz | No | No |
| 192.168.40.0/24 | Local IoT | Wi-fi: SSID 3 | 2.4GHz | Yes | Not Applicable |
| Cloud IoT | 2.4GHz | Yes |
With the design finished, it is time to implement it in the UDR:
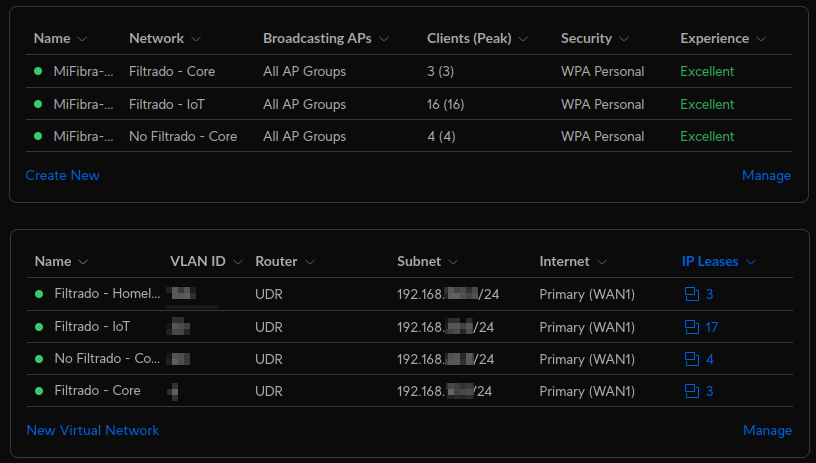
Once all devices are connected to the assigned networks, the basis for segmentation are set, but it is very important to realize that at this point there is no real segmentation going on, as Unifi equipment sets the default firewall rules for inter VLAN communications to Allow.
Therefore, in following posts, I will discuss how to:
- Deploy a recursive DNS filtering setup
- Route some Internet traffic Internet traffic through a VPN
- Limit communication channels using firewall rules
- Describe how to set up a Homelab
Stay tuned for further updates!